Gmssl openssl国密网络传输加密
要不是因为要做这方面的应用估计是不会写这边文章了,因为从小白开始始终还是不容易的,里面有不对的地方还请大家多多吐槽
要不是因为要做这方面的应用估计是不会写这边文章了,因为从小白开始始终还是不容易的,里面有不对的地方还请大家多多吐槽。
好了言归正传,作为一名网工,加密传输是必不可少的课题,这次接触了一个小课题,通过Gmssl 工具与OpenSSL 完成基于SM2国密数字证书及基于SM2证书的SSL/TLS集成,在这里我先暂时用集成,因为包括Gmssl与OpenSSL都是由国内与国际的专门组织维护,我只是拿来主义幸好都是开源的,在国内百度的时候真心没有找到一篇完整的或者完全的集成文章,所以打算整理一下,写个完整的流程(当然我也是个比较懒的人能省略的都推其他大神的文章了)也感谢他们的分享
我会分为四个步骤:
1、Gmssl的编译
2、OpenSSLN的编译
3、SM证书的生成
4、测试
5、抓包查看密钥协商过程
1、Gmssl的编译:
先介绍一下环境:
2台虚拟机 一台作为服务端,一台作为客户端
用的是Oracle的vbox 为了方便测试 将创建后的两台虚拟机桥接在同一张物理网卡上
系统环境 server与client 端采用的都是centos 7 3.10.0-1160.el7.x86_64
下载Gmssl
关于GmSSL
点击Download 将下载的包文件上传到centos目录
或者 wget https://github.com/guanzhi/GmSSL/archive/master.zip
yum install gcc unzip 等编译需要的基础环境与工具
编译安装请参考
最后 openssl version
出现下面的提示就表示Gmssl编译安装并运行成功了
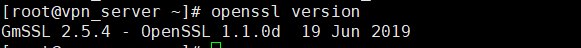
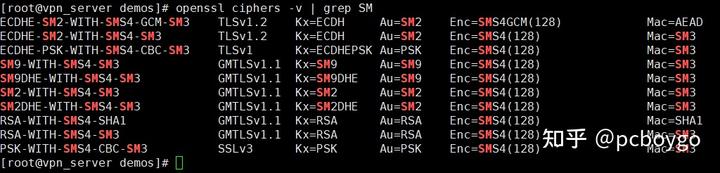
通过 openssl ciphers -v | grep SM
2、OpenN编译
首先下载 OpenN源码
https://openvpn.net/community-downloads/上面这个网站打开有点慢
我下载的是 openN-2.5.3
编译安装前先安装如下依赖
yum install epel-release
yum install -y openssl-devel lzo lzo-devel pam pam-devel automake pkgconfig makecache
tar -zxvf openN-2.5.3.tar.gz #是不是可以直接yum open**n 个人觉得也是可以的但是没有实际操作过
cd open**N-2.5.3
./configure
make && make install
不出意外可以在 /usr/local/sbin 目录下查看到 可执行的open**N文件
两台虚拟机同样的编译工作在这里结束了,注意两台虚拟机的编译过程都是一样的
如果是实验环境 建议在这里直接克隆一台一模一样的
3、生成证书
证书生成参考
2.证书生成准备:
在 home 目录下 make dir apps/demoCA/
cd apps/demoCA/
mkdir certs crl newcerts private
touch index.txt
echo "01" > serial
3.生成根证书:
gmssl ecparam -genkey -name sm2p256v1 -text -out Root.key #生成私钥
gmssl req -new -key Root.key -out Root.req #证书请求
gmssl x509 -req -days 3650 -sm3 -in Root.req -signkey Root.key -out RootCA.crt #生成根证书
4.生成服务端证书
gmssl ecparam -genkey -name sm2p256v1 -text -out Server.key #生成私钥
gmssl req -new -key Server.key -out Server.req #证书请求
gmssl x509 -req -sm3 -days 3650 -CA RootCA.crt -CAkey Root.key -CAcreateserial -in Server.req -out ServerCA.crt #签发证书
gmssl verify -CAfile RootCA.crt ServerCA.crt #证书验证
gmssl x509 -in ServerCA.crt -text -noout #查看证书
5.生成客户端证书
gmssl ecparam -genkey -name sm2p256v1 -text -out Client.key #生成私钥
gmssl req -new -key Client.key -out Client.req #证书请求
gmssl x509 -req -sm3 -days 3650 -CA RootCA.crt -CAkey Root.key -CAcreateserial -in Client.req -out ClientCA.crt #签发证书
gmssl verify -CAfile RootCA.crt ClientCA.crt #证书验证
gmssl x509 -in ClientCA.crt -text -noout #查看证书
6.客户端/服务端通信验证
gmssl s_server -accept 443 -key Server.key -cert ServerCA.crt -dkey Server.key -dcert ServerCA.crt -CAfile RootCA.crt -msg -debug #服务端
gmssl s_client -connect 127.0.0.1:443 -key Client.key -cert ClientCA.crt -CAfile RootCA.crt -msg -debug #客户端
验证通过以后就可以开始采用 国密加密算法来加密**N隧道了
4、使用编译好的openN 进行国密加密算法验证:
1、首先启动服务端

dh2048.pem ta.key 如果不想自己生成,可以直接在open**N源码中找到
服务端的config文件需要修改的地方我先贴出来
[root@gm**N opt]# more open**N/server.conf nn;tls-auth /opt/open**N/ta.key 0 # This file is secretnn# Select a cryptographic cipher.n# This config item must be copied ton# the client config file as well.n# Note that v2.4 client/server will automaticallyn# negotiate AES-256-GCM in TLS mode.n# See also the ncp-cipher option in the manpagen# cipher AES-256-CBCncipher SMS4-CFBnn
在 /user/local/sbin 下找到open**N执行文件
[root@gm**Nsbin]# ./open**N --config /opt/open**n/server.conf
2021-09-19 10:06:50 WARNING: --topology net30 support for server configs with IPv4 pools will be removed in a future release. Please migrate to --topology subnet as soon as possible.n2021-09-19 10:06:50 DEPRECATED OPTION: --cipher set to 'SMS4-CFB' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future Open**n version will ignore --cipher for cipher negotiations. Add 'SMS4-CFB' to --data-ciphers or change --cipher 'SMS4-CFB' to --data-ciphers-fallback 'SMS4-CFB' to silence this warning.n2021-09-19 10:06:50 WARNING: file '/opt/open**N/server.key' is group or others accessiblen2021-09-19 10:06:50 Open**N 2.5.3 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Aug 17 2021n2021-09-19 10:06:50 library versions: GmSSL 2.5.4 - OpenSSL 1.1.0d 19 Jun 2019, LZO 2.06n2021-09-19 10:06:50 net_route_v4_best_gw query: dst 0.0.0.0n2021-09-19 10:06:50 net_route_v4_best_gw result: via 172.16.15.254 dev em1n2021-09-19 10:06:50 Diffie-Hellman initialized with 2048 bit keyn[GMTLS_DEBUG] set sm2 signing certificaten[GMTLS_DEBUG] set sm2 signing private keyn2021-09-19 10:06:50 Initialization Sequence Completedn
服务端启动完毕
2、客户端启动
客户端配置文件
[root@client sbin]# more /opt/open**N/client.conf n##############################################n# Sample client-side Open**N 2.0 config file #n# for connecting to multi-client server. #n# #n# This configuration can be used by multiple #n# clients, however each client should have #n# its own cert and key files. #n# #n# On Windows, you might want to rename this #n# file so it has a .o**n extension #n##############################################nnn
启动客户端
[root@client sbin]# ./open**N --data-ciphers SMS4-CFB --auth-nocache --config /opt/open**N/client.conf
--data-ciphers SMS4-CFB 加这个参数是让客户端与服务端在第二阶段加密隧道协商时采用 SMS4-CFB 对称算法
--auth-nocache 这个参数是不让认证信息留存在 计算机的缓存中,避免安全风险
./open**N --data-ciphers SMS4-CFB --auth-nocache --config /opt/open**N/client.conf n[root@client sbin]# ./open**N --data-ciphers SMS4-CFB --auth-nocache --config /opt/open**N/client.conf n2021-09-19 10:15:37 WARNING: file '/opt/open**N/client.key' is group or others accessiblen2021-09-19 10:15:37 Open**N 2.5.3 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Jul 25 2021n2021-09-19 10:15:37 library versions: GmSSL 2.5.4 - OpenSSL 1.1.0d 19 Jun 2019, LZO 2.06n2021-09-19 10:15:37 WARNING: No server certificate verification method has been enabled. See http://open**N.net/howto.html#mitm for more info.n[GMTLS_DEBUG] set sm2 signing certificaten[GMTLS_DEBUG] set sm2 signing private keyn2021-09-19 10:15:37 TCP/UDP: Preserving recently used remote address: [AF_INET]58.20.231.166:61568n2021-09-19 10:15:37 Socket Buffers: R=[212992->425984] S=[212992->425984]n2021-09-19 10:15:37 UDP link local: (not bound)n2021-09-19 10:15:37 UDP link remote: [AF_INET]58.20.231.166:61568n2021-09-19 10:15:37 TLS: Initial packet from [AF_INET]58.20.231.166:61568, sid=8ec4ffb1 a71702a0n2021-09-19 10:15:37 VERIFY OK: depth=1, C=CN, ST=Hunan, L=xiangtan, O=Hunanshutong, OU=ca, CN=can2021-09-19 10:15:37 VERIFY OK: depth=0, C=CN, ST=Hunan, L=xiangtan, O=Hunanshutong, OU=server, CN=servern2021-09-19 10:15:37 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-SM2-WITH-SMS4-SM3, peer certificate: 256 bit EC, curve sm2p256v1, signature: SM2Sign-with-SM3n2021-09-19 10:15:37 [server] Peer Connection Initiated with [AF_INET]58.20.231.166:61568n2021-09-19 10:15:37 PUSH: Received control message: 'PUSH_REPLY,route 1.1.1.0 255.255.255.0,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5,peer-id 0,cipher SMS4-CFB'n2021-09-19 10:15:37 OPTIONS IMPORT: timers and/or timeouts modifiedn2021-09-19 10:15:37 OPTIONS IMPORT: --ifconfig/up options modifiedn2021-09-19 10:15:37 OPTIONS IMPORT: route options modifiedn2021-09-19 10:15:37 OPTIONS IMPORT: peer-id setn2021-09-19 10:15:37 OPTIONS IMPORT: adjusting link_mtu to 1640n2021-09-19 10:15:37 OPTIONS IMPORT: data channel crypto options modifiedn2021-09-19 10:15:37 Outgoing Data Channel: Cipher 'SMS4-CFB' initialized with 128 bit keyn2021-09-19 10:15:37 Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authenticationn2021-09-19 10:15:37 Incoming Data Channel: Cipher 'SMS4-CFB' initialized with 128 bit keyn2021-09-19 10:15:37 Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authenticationn2021-09-19 10:15:37 net_route_v4_best_gw query: dst 0.0.0.0n2021-09-19 10:15:37 net_route_v4_best_gw result: via 192.168.58.1 dev enp0s3n2021-09-19 10:15:37 ROUTE_GATEWAY 192.168.58.1/255.255.255.0 IFACE=enp0s3 HWADDR=08:00:27:40:f3:90n2021-09-19 10:15:37 TUN/TAP device tun0 openedn2021-09-19 10:15:37 net_iface_mtu_set: mtu 1500 for tun0n2021-09-19 10:15:37 net_iface_up: set tun0 upn2021-09-19 10:15:37 net_addr_ptp_v4_add: 10.8.0.6 peer 10.8.0.5 dev tun0n2021-09-19 10:15:37 net_route_v4_add: 1.1.1.0/24 via 10.8.0.5 dev [NULL] table 0 metric -1n2021-09-19 10:15:37 net_route_v4_add: 10.8.0.1/32 via 10.8.0.5 dev [NULL] table 0 metric -1n2021-09-19 10:15:37 Initialization Sequence Completedn
启动后可以看到几个信息
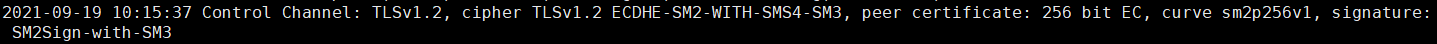
第一阶段 tls协商采用的算法为 ECDHE-SM2-WITH-SMS4-SM3
2021-09-19 10:15:37 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-SM2-WITH-SMS4-SM3, peer certificate: 256 bit EC, curve sm2p256v1, signature: SM2Sign-with-SM3
第二阶段 数据传输隧道加密算法为 SMS4-CFB
2021-09-19 10:15:37 OPTIONS IMPORT: data channel crypto options modified
2021-09-19 10:15:37 Outgoing Data Channel: Cipher 'SMS4-CFB' initialized with 128 bit key
2021-09-19 10:15:37 Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
2021-09-19 10:15:37 Incoming Data Channel: Cipher 'SMS4-CFB' initialized with 128 bit key
这样基于国密算法的OPEN**N环境就搭建好了
5、国密算法加密隧道验证
采用wirshake抓包查看采用的加密算法:
在客户端或服务端,采用tcpdump 进行抓包,将抓包文件 用wirshake进行分析
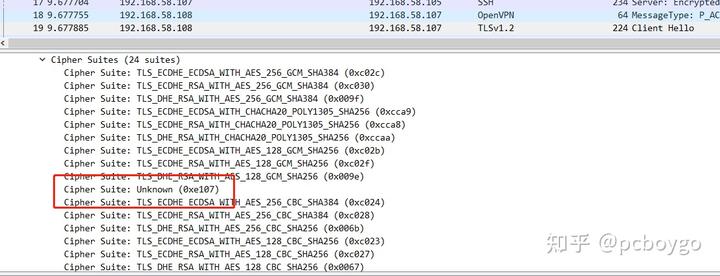

并申明签名算法为
algorithmIdentifier (iso.2.156.10197.1.501)
Algorithm Id: 1.2.156.10197.1.501 (iso.2.156.10197.1.501)
通过算法标识符查看对应的算法
OIDs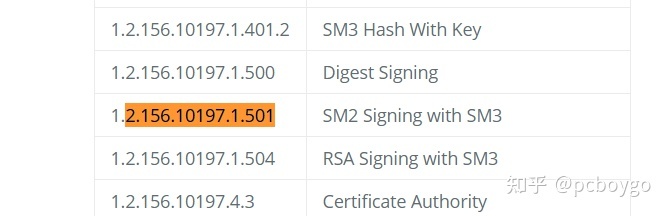
找到以后确认双方第一阶段秘钥协商签名算法采用的是 signature: SM2Sign-with-SM3
ECDHE-SM2-WITH-SMS4-SM3
暂时先写到这里,希望大拿们有时间帮我多指正,在这里感谢 git上的大佬,感谢国内http://bing.com 与 GMssl团队。
这个实验踩了无数坑,所以总结一下,在知乎发片文章
国产化编译参考以下链接
国产化飞腾架构银河麒麟编译国密算法加密隧道 - pcboygo的文章 - 知乎 https://zhuanlan.zhihu.com/p/609963252
上一篇:HSP-15是一种高速工具钢
下一篇:OU2562S型显微维氏硬度计








